CONTINUUM CYBER
CYBER SECURITY EVOLVES EVERY MINUTE
95% of cybersecurity breaches are caused by human error.

Fact:
62% of SMEs experienced a cyber incident in 2021 according to the latest data here in Australia.Fact:
Over 67,500 cybercrime reports, an increase of nearly 13 per cent from the previous financial year.Fact:
Self-reported losses from cybercrime total more than $33 billion.Fact:
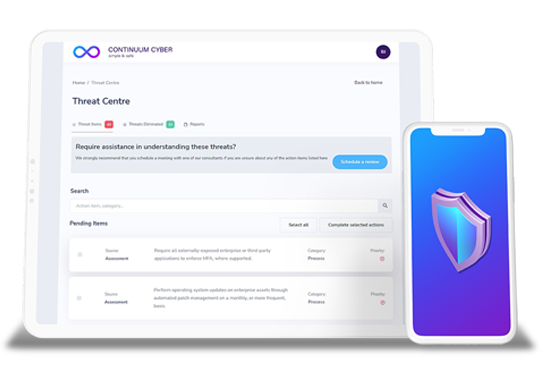
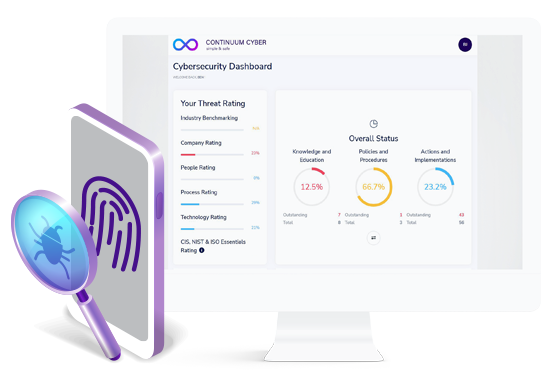
Fraud, online shopping scams and online banking scams were the top reported cybercrime types.UNDERSTAND YOUR RISK PROFILE WITH OUR REVOLUTIONARY PLATFORM
With so much at risk to your business in these times, we partner to take a deep dive into your people, your processes and technology.


TOGETHER WE CAN:
- Identify your current risks against local and international best practice.
- Design and conduct bespoke Phishing campaigns to highlight your staff’s ability to spot a malicious email.
- Train your staff in an easy and traceable way to empower them to become the first line of defence for your business.
WE PROVIDE & ASSIST BY:
- Generating processes and policies to create a transparent cybersecurity culture in your organisation.
- Are on call to help 24/7 incident response line to be there when it matters in the event of an event.
- Have access to Cyber security experts that work hard for your business to eliminate the ever-changing risks.
OUR SERVICES
Alongside our proprietary platform we offer a suite of services to assist you in your mission of creating a robust security posture for your business.
We use the same mythologies, tool and tactics as a real world attacker to sure up your defences and protect your business and reputation.
Penetration Testing
Expert support to test and uncover issues and risks across applications, cloud, networks, systems, and devices, with comprehensive guidance on remediation options and advice.
• Web Application Penetration Testing
• Web Services Penetration Testing
• External Network Penetration Testing
• Internal Network Penetration Testing
• Mobile Application Penetration Testing
• Wireless Penetration Testing
• Physical Penetration Testing
• SCADA / OT and IoT Penetration Testing
• Social Engineering Assessment
• Thick Client Penetration Testing
• OSINT Assessment
• Managed Penetration Testing
Tabletop Excersise
Get prepared- are you ready for an attack?
The Tabletop Exercise is discussion-based and provides an incident scenario that has been tailored to your unique environment and operational needs. Our experts facilitates a discussion with your response team that includes the actions that are required, who is responsible for them, who needs to be notified and how to coordinate these multiple moving parts.
Application Security
Comprehensive application security services, reviews and assessments to ensure your application code is strong enough to withstand global cyber threats.
• SDLC maturity review
• DevSecOps consulting
• Secure development standards definition
• Source code review
• Application log enrichment for ingestion into SIEM solutions
• Threat modelling
Vulnerability Assessments
Gain a high-level and cost effective technical and hands-on assessment of your security posture with a focus on vulnerabilities that can impact your organisation or solution.
• Network and infrastructure vulnerability assessment
• Web application vulnerability assessment
Technical Assessments
Gain a holistic understanding of the potential impact an attacker can have on your cloud and IT infrastructure, operations technology, IoT solutions and more.
• Cloud technology assessment
• Operational technology assessment
• Industrial Control Systems testing
• IoT assessment including hardware, software and end-to-end solutions
Red/Purple Team Testing
Expert testing of your digital, physical and workforce environments with a simulated cyber-intrusion using real-world attack methods specific to your unique environment and guidance to assess vulnerabilities and how to safeguard against future attacks. We help you prepare for the worst to stop
• Red team assessments
• Blue team assessments
CONTINUUM CYBER SOFTWARE PRICING
POA
1-19 Users
-
- Get real-time insights.
- Work directly with our experts.
- Create a concise plan with our team.
- Meet monthly with a cyber professional.
- Access to valuable resources.
POA
20-50 Users
- Get real-time insights.
- Work directly with our experts.
- Create a concise plan with our team.
- Meet monthly with a cyber professional.
- Access to valuable resources.
POA
50-250 Users
- Get real-time insights.
- Work directly with our experts.
- Create a concise plan with our team.
- Meet monthly with a cyber professional.
- Access to valuable resources.
BLOG
CYBER SECURITY IS FUNDAMENTAL IN THE POST COVID WORLD.
Read our latest articles written by experts addressing current issues in the digital space.